Gitlab SSO OIDC Setup
Clone Docker Toolkit (Optional)
If not already done clone the docker toolkit repo
git clone https://gitlab.com/D3vbd/docker-toolkit.git ~/docker-toolkit
This will setup the toolkit in the folder ~/docker-toolkit.
We will be using the vault folder.
~/docker-toolkit/vault
Gitlab Application
In your Gitlab Group go to
Settings -> Applications
- Create a new application
vault
Set the redirect uris.At least 1 is required.
https://localhost:8200/ui/vault/auth/gitlab-oidc/oidc/callback
https://vault.localhost:8200/ui/vault/auth/gitlab-oidc/oidc/callback
https://vault.svc.D3vbd:8200/ui/vault/auth/gitlab-oidc/oidc/callback
-
Uncheck Confidential
-
Add Scopes
- openid
- profile
Copy Down the Client ID and Secret
Setup Vars
export GITLABCI_AUTH_PATH="gitlab-oidc"
# Vault address
export VAULT_ADDR="https://vault.localhost:8200"
## Can add more
export REDIRECT_URI="$VAULT_ADDR/ui/vault/auth/$GITLABCI_AUTH_PATH/oidc/callback"
export LOCALHOST_REDIRECT_URI="https://localhost:8200/ui/vault/auth/$GITLABCI_AUTH_PATH/oidc/callback"
export PROD_REDIRECT_URI="https://vault.svc.d3vbd:8200/ui/vault/auth/$GITLABCI_AUTH_PATH/oidc/callback"
### root token from startup
### or a token if you have enabled a different auth method
export VAULT_TOKEN=""
###### Gitlab Application
export CLIENT_ID=""
export CLIENT_SECRET=""
Enable OIDC
vault auth enable -path=$GITLABCI_AUTH_PATH oidc
vault write auth/$GITLABCI_AUTH_PATH/config \
bound_issuer="https://gitlab.com" \
oidc_discovery_url="https://gitlab.com" \
default_role="admin" \
oidc_client_secret="$CLIENT_SECRET" \
oidc_client_id="$CLIENT_ID"
Create Auth Role
Policy
# Path to admin policiy
vault write sys/policy/admin policy=@./vault/policies/admin.hcl
Role
set the bound claims group to your gitlab group.
I am using all 3 urls for allowed redirects. feel free to change or just use $REDIRECT_URI
vault write auth/gitlab-oidc/role/admin - <<EOF
{
"user_claim": "email",
"allowed_redirect_uris": [
"$REDIRECT_URI",
"$LOCALHOST_REDIRECT_URI",
"$PROD_REDIRECT_URI"
],
"bound_audiences": "$CLIENT_ID",
"oidc_scopes": "openid,email,profile",
"role_type": "oidc",
"policies": ["default","admin"],
"ttl": "1h",
"bound_claims": { "groups": ["D3vbd"] }
}
EOF
Repeat for adding new roles to the auth method. The admin role should give you full access.
Show on Login
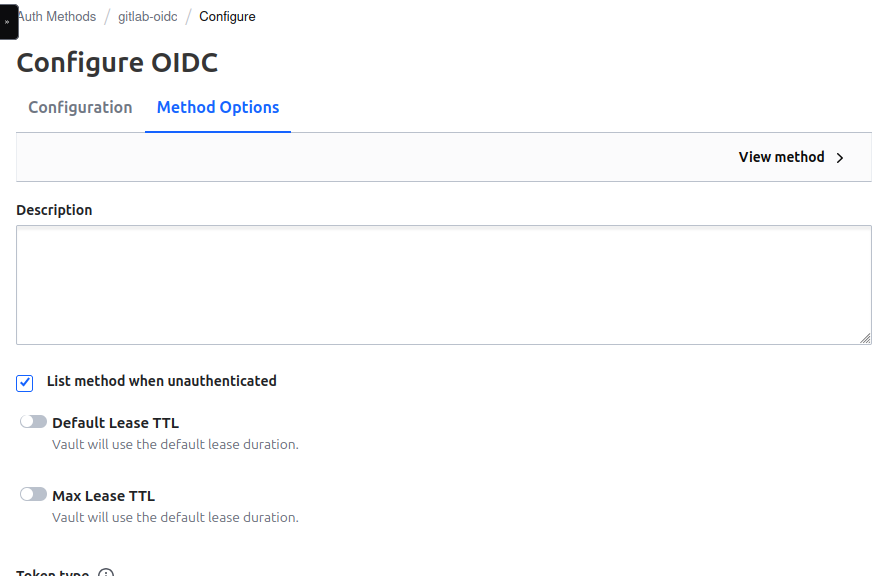
To get this to appear on login, go into the UI and edit the auth methods options.
make sure List method when unauthenticated is checked. Save and re-login.